There are a lot of organizational Tactics, Techniques, and Procedures (TTPs) in Counterintelligence (CI) that can inform more efficient Defensive Cyber Operations (DCO) or more generally Computer Network Defense (CND) 1 processes and strategies. While the mapping is not perfect, it would be interesting to explore further how traditional CI organization can collaborate with information security groups. A perfect first step into this direction would be setting up better information sharing activities between CI and CND to assist in identifying and neutralizing insider activities: getting deep insight on potential bad actors inside an organization can help the defensive team to architect and deploy better monitoring and accounting systems in a targeted way. In the private sector, this would mean a very close collaboration between the human resources department and the security office.
Hypothesis: CND → CI|Cyber
Computer Network Defense was until May 2013 defined in the context of military operations as:
Actions taken through the use of computer networks to protect, monitor, analyze, detect and respond to unauthorized activity within Department of Defense information systems and computer networks.
This definition is mutatis mutandis very much applicable to how non-military domains approach information systems security. While not comprehensive (what is ever in security?), it scopes the area of activity for the security professional fairly nicely, especially if you include notions of addressing the insider threat and resilience (i.e. the capability to operate under attack).
Here is a proposition: The mapping from Computer Network Defense to the restriction of Counter Intelligence to the Cyber domain is a monomorphism:
CND → CI|Cyber
While this is not a strict mapping in the sense in which mathematical morphisms are defined, it is really intended to say this: the methods and procedures used in CND are very similar to those that are used for the application of counterintelligence to investigating information systems.
CI and CND Activities
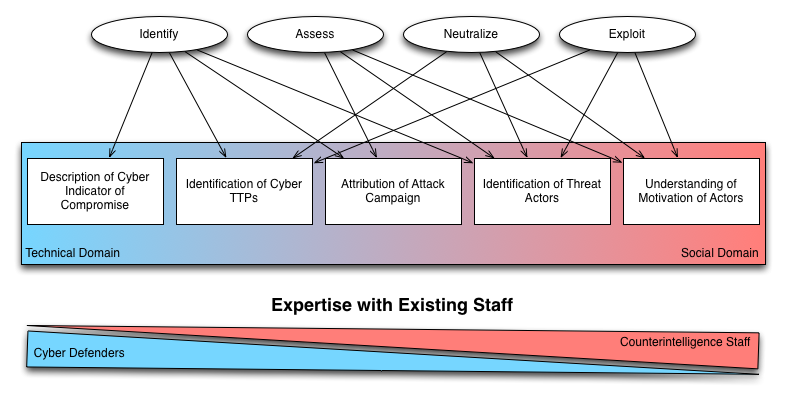
How can you make this argument? In a recent article by Michelle Van Cleave2 describes the general field of CI. Specifically, she illustrates the areas where CI is active:
- Identify
- Assess
- Neutralize
- Exploit
Looking at any effective security program, most of these areas are very relevant to the network defender:
1. Identify
Similar to the need of CI to “identify the foreign intelligence activities directed against the United States”3, including attribution, types of activities, targets, etc., network defenders (both public and private sector) need to better understand the threat landscape that they are facing. Identifying the threat actors and their goals is a necessary prerequisite for all subsequent activities in defending against attacks for both CI and CND: The similarities in identifying the adversary in both fields seems obvious, and on closer inspection requires similar approaches.
This becomes especially striking in the context of identifying insider threats. Indeed, dealing with insider threats — the heart of any CI activity — presents the tightest mapping between CI and CND across many of the areas discussed here. Historically, CI organizations have had severe challenges with Insider Threats, and some of these challenges are likely due to the disconnect between the CI organization’s goal and the monitoring capabilities that were available.
2. Assess
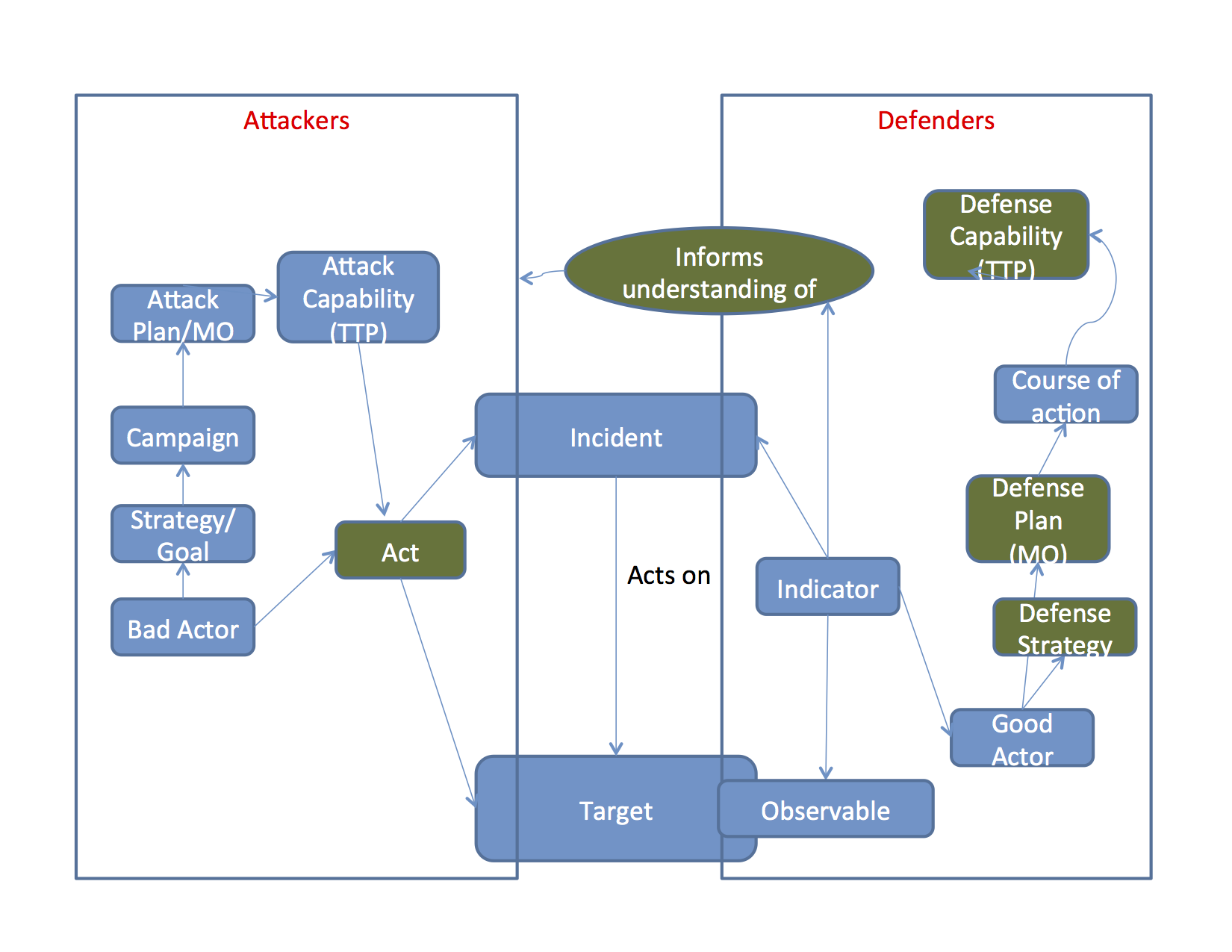
As for CI, it is important for information systems security to accurately assess the situation. The awareness of threats and the understanding of how they may affect critical assets is very important for the identification of the actual risks, and the development of effective countermeasures to limit the potential impact from those threats or – alternatively – accept the risk consciously. In CND, threat and subsequent risk assessments are the departure point for formulating the defensive strategy. This activity also encompasses the analysis of the Attacker’s business processes and intention from a Defender’s perspective. In the figure below, this analysis informs the understanding of the box on the left side by the analyst (“Good Actor”) on the right.
3. Neutralize
Once the threat is clearly characterized, both CI and CND need to address it and determine the best treatment for the risk it poses. While CI – based on the broad set of tools legally available to them – can be much more effective, CND and its more limited means aim to neutralize the threat as well. Regular defensive tools can deny the adversary access to the assets that they seek. In addition they can blind the reconnaissance activities of attackers by minimizing the cyber profile of the targets, or respond to attacker’s probe requests with wrong data.
A significant advantage for CI is that they have a wide arsenal of offensive capabilities such as search warrants and trained investigators that do not necessarily translate into similar tools for CND, at the least for private sector organizations. For public sector organizations, other means (such as Computer Network Attack – see reference in footnote 1) are available as additional approaches to neutralize the threat. Some approaches such as using honeypots for deceiving the adversary are acceptable in certain circumstances, but “active defense” is a very much still a legal gray area: cyber vigilantism is not currently acceptable in most regulatory regimes.
With both the threat actors and the targets under the control of the defender (such as in the case of the insider threat), the possibilities for neutralizing insider threats are less constrained, even in the private sector. Concerns restricting active defense against an outsider, such as risks of imperfect identification and collateral damage, are less pressing. Fairly heavy-handed interdiction or quarantine — up to confiscation of resources and physical restraint of the (human) attacker — may be possible. At the same time, any activities along such lines would have to be carefully orchestrated to not run afoul of legal limitations.
4. Exploit
Exploitation of the attacker’s weaknesses is typically not within the scope of CND, but would be covered by Computer Network Exploitation (CNE) and subsequent Computer Network Attacks (CNA) in the sense of JP 3-13. Again, to a limited extent private sector defenders are engaging in these activities when they take an “Active Defense” position, which is much less common and may have legal repercussions for the defending side. Again, there may be greater latitude here in dealing with insider threats. While considerations such as preservation of evidence can put prudential limitations on exploiting attacker-controlled systems operating “inside” the defender, the general legal prohibitions on unauthorized access to systems will not apply.
Discussion
The mapping discussed above seems fairly straightforward, but there are a number of additional aspects that should be considered. Initially, it is important to investigate what type of expertise is expected to perform tasks associated with identification, assessment, neutralization, and exploitation in either CND or CI. As such it may be helpful to visualize how specific expertise has been common in either discipline:
While this mapping is not particularly accurate and leaves out a number of more complex aspects in either CND or CI, it still illustrates how the two disciplines may effectively cooperate. One prerequisite for successful collaboration is a shared understanding of how responsibilities should be assigned and what the core concepts really mean (i.e. a shared ontology). Creating a mapping between CND and CI activities may assist is establishing this joint understanding4.
For large organizations the CND and CI functions may be implemented in different groups, leading to specialization and the danger of disconnectedness from each other. For example, traditional CI in national security has in the past mainly focused on the Social Domain and indicators derived from HUMINT and related disciplines. On the other hand, CND has in the past often operated in a “CI vacuum”, i.e. without considering motivations, psychological aspects, and other elements of the Social Domain when trying to defend cyber assets.
Smaller or private sector organizations typically do not have the resources to operate separate CND and CI groups. Instead, these functions are typically implemented by a security office or – less ideally – scattered across the entire organization between human resources, IT staff, marketing/business intelligence, and operational staff.
—
Thanks to Richard, Grant, Mike, John, Rick, John, and KP for feedback.
1 CND was formally defined in Joint Publication 3-13 until May 2013 at http://www.dtic.mil/doctrine/new_pubs/jp3_13.pdf. For the purpose of this article, I am also using it in a more general sense, i.e. the practice of defending any information system against attackers.
2 Michelle Van Cleave, “What is Counterintelligence?”, The Intelligencer: Journal of U.S. Intelligence Studies, Fall/Winter 2013, 2014
3 ibid.
4 Interestingly enough, this approach and the identification of specific conceptual domains echos modern understanding in Command and Control (C2) theory: Davis Alberts has discussed a modern model for C2 in which he identifies how different conceptual domains are necessary for developing an understanding of the battle space and creating plans and executing them. Alberts’ Social Domain mainly comprises the social interactions and relationships of the friendly force’s members, but in order to better understand the adversary it seem natural to extend the Social Domain to all participants, including adversaries and neutral entities. See e.g. David Alberts, “Understanding Command and Control”, CCRP Publication Series, 2006. Note that Alberts differentiates between Information Domain and Physical Domain. For the purpose of discussing CND, the Cyber Domain will need to be treated on the same basis as the physical domain, since this is the space where actions can be performed and effects can be observed. The Information Domain is about the communication space – Cyber only enters this picture by enabling an effective Information Domain.