This week, we made some pretty good progress toward formalizing the conceptual threat modeling work at OMG:
OMG SysA Meeting
On Wednesday the team presented the result of the last 3 months of work on the conceptual threat model (please find the presentation here). Overall, we have explored the problem area and have started to develop a decent understanding of how a specification would need to be written in order to enable semantic interoperability across different domain and protocol stacks.
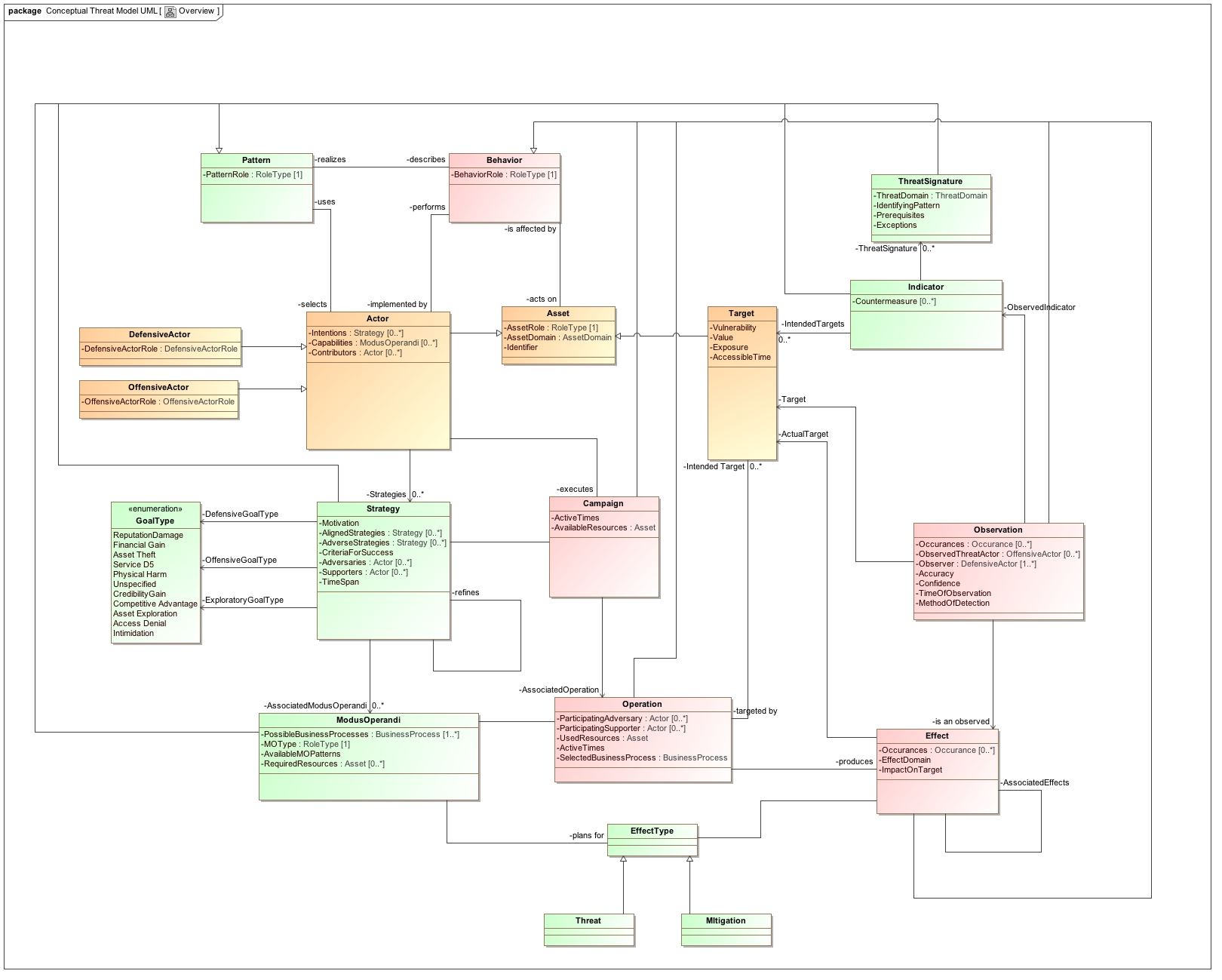
In general, the conceptual model we are working on will describes the abstract concepts within the overall problem space of threat and risk modeling. With such a model, semantic mappings to specific logical models (such as the the cyber-domain specific model that STIX is creating) can be generated. This will allow the automated generation of ‘semantic glue’, i.e. mappings that transform different representations of data. The benefit of using a conceptual model lies in the fact that it is independent of the respective underlying logical models for each domain or protocol. This approach has been around for some time now, but it is currently formalized in the Semantic Information Modeling for Federation (SIMF) project.
Currently, we have a (very early) draft model up on our GitHub project page which captures some of the most important aspects of the model:
- Domain agnostic concepts – all elements of the model can be equally applied to any threat domain. Currently, we are trying to capture the domain identification through an enumeration containing biological, chemical, cyber, electromagnetic, human, physical, and other domains. Eventually, this should be an extension point to the model.
- Symmetry of offense and defense – all elements of the model can be instantiated by offensive and defensive entities. In fact, we expect that more complex scenarios will invariably leverage both offensive and defensive capabilities across they strategies and campaigns. One example would be using offensive elements in a defensive strategy, in order to implement an ‘active defense’ philosophy.
- Identification of assets, patterns, and behaviors – all significant elements in the model are either assets (‘things’), patterns (‘plans’), or behaviors (‘events’). In this way, patterns are realized by behaviors, most commonly through the activity of actors.
The model itself lends itself fairly cleanly for extension to safety modeling as well: for example, natural disaster would be modeled through Operations with specific Effects, but without (offensive) Actors with Strategies or M.O.s.
As part of the review of the body of work, we decided to join forces with another emerging project on Risk Management within the Systems Assurance TF. The goal will be to produce a joint RFP in time for the June 2014 OMG meeting, and the commence the full specification development.
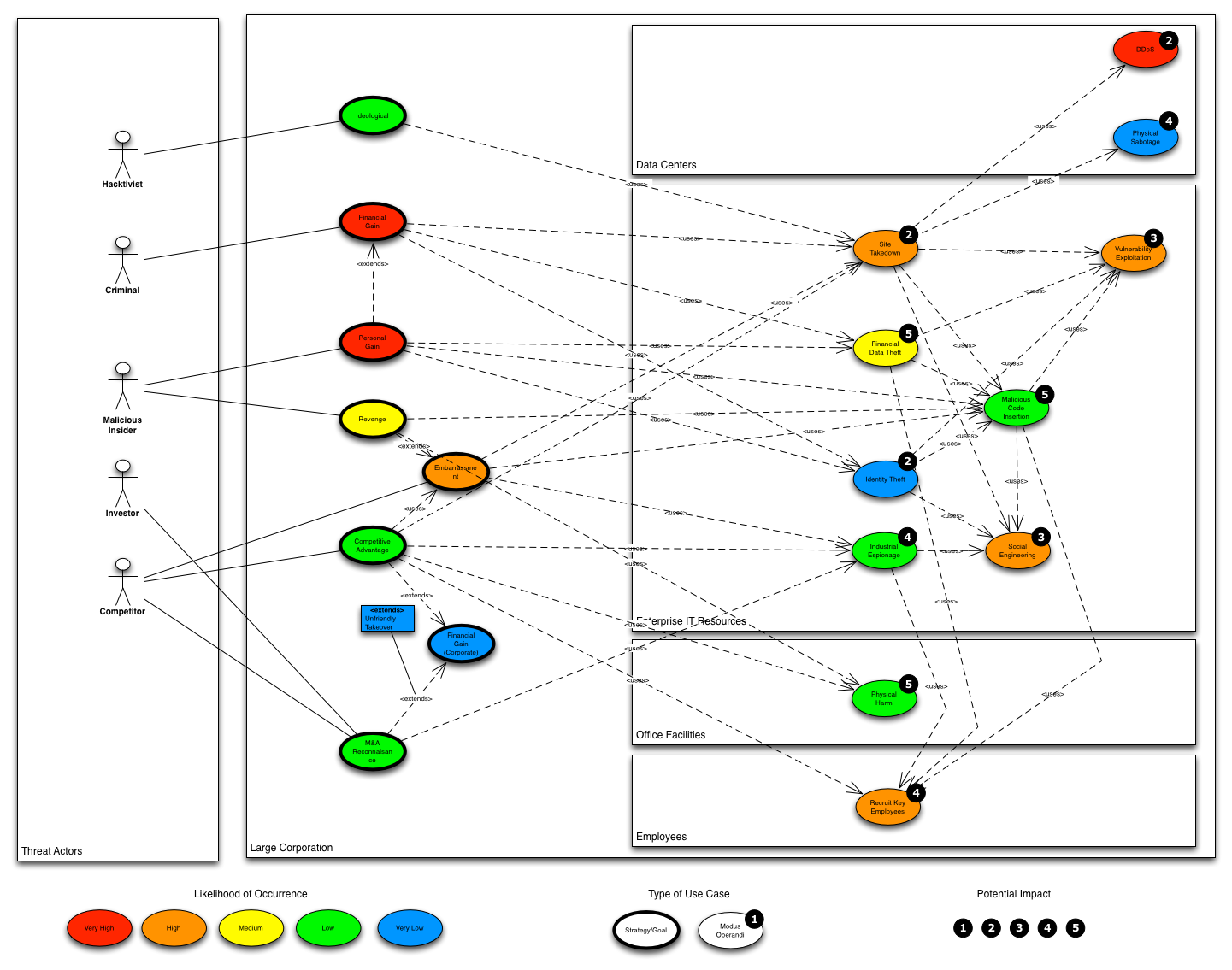
The reason for combining forces with the risk management project is fairly clear: a conceptual threat model will be significantly more useful if a risk metric can be associated in a repeatable way. Metricizing the threat space this way will allow a number of interesting applications, even beyond pure risk management. A way to leverage this in modeling is by identifying the threats in a use case diagram like this:
Another one of the ideas raised in earlier discussion was to use the model for simulation. In this application, an experimenter can evaluate a large number of threat scenarios by averaging over the threat and environmental parameters using Monte-Carlo methods and then test the effectiveness of different defensive strategies. If the threat model is metricized with a stable risk methodology, the implementation and evaluation of such simulations can be much more effective.
WIS3 – Threat Panel
On Thursday, we participated in the annual WIS3 conference hosted by IJIS, PM-ISE, and OMG. We had a great panel consisting of representatives from the public and private sector:
- Greg Rattray, Delta Risk
- Antonio Scurlock, ESSA, DHS
- Any Pendergast, Cyber Squared
- Justin Stekervetz, NIEM PMO, DHS
- Cory Casanave, Model-Driven Software
With the perspective of the panelists, we were able to discuss the current state of threat sharing and its implications for national security, retail, law enforcement, and other domains. The discussions touched history, current state, and future of threat modeling, and the different initiatives in this area can help implementors in moving forward. One of the great takeaways of the workshop was the announcement of the Project Interoperability initiative by PM-ISE that aims at creating a community for enabling information sharing projects, and serves as a launch point to various development sites.